Table of contents
ConfigMap
ConfigMap is a way to store configuration settings for applications running in Kubernetes. It's like a dictionary that holds key-value pairs of configuration data.
Imagine you have an application that requires some settings, like a database URL, API keys, or any other parameters. Instead of hardcoding these values into your application's code, you can create a ConfigMap to store them separately.
The ConfigMap can be created using a configuration file and applied to the Kubernetes cluster. Once created, your application can access the configuration values from the ConfigMap. It's like your application asking Kubernetes for the values it needs.
You can use these configuration values in different ways. For example, you can set them as environment variables, which are like variables that your application can read. Alternatively, you can mount the ConfigMap as a file, allowing your application to read the values from that file.
The benefit of using a ConfigMap is that it separates the configuration from the application code. So, if you need to change a configuration value, you can update the ConfigMap without modifying and redeploying the application. It makes managing configurations easier, especially when you have multiple applications running in a Kubernetes cluster.
Example of a configMap.yml file
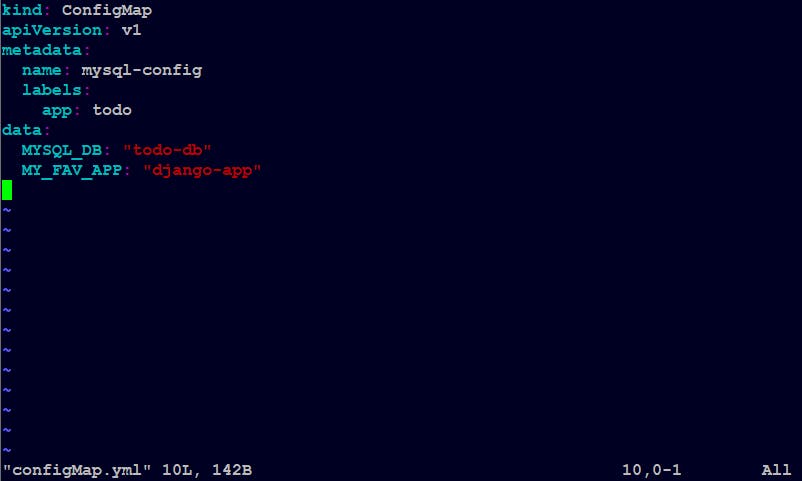
Apply the configmap file with the "apply" command:
Kubectl apply -f configMap.yml

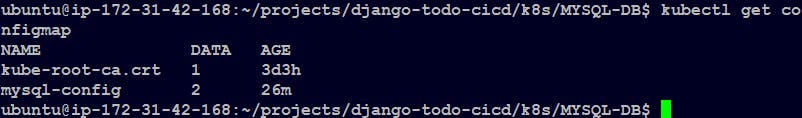
We can check our configmap with the following command:
kubectl get configmap
Secret
Secret is an API resource that is used to store and manage sensitive information, such as passwords, API keys, and certificates. It provides a way to securely store and distribute this sensitive data to the applications running within a Kubernetes cluster.
You can create a Secret in Kubernetes by defining it in a YAML or JSON file and applying it to the cluster using the kubectl apply command.
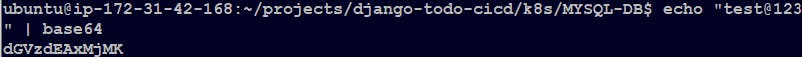
Before we make secret.yml file let's create and encode a password first, we can do so using "base64"
Encoding a password with base64
echo "yourpassword" | base64
Now, copy the encrypted password and paste it into the value against the key "password" in the secret.yml file.
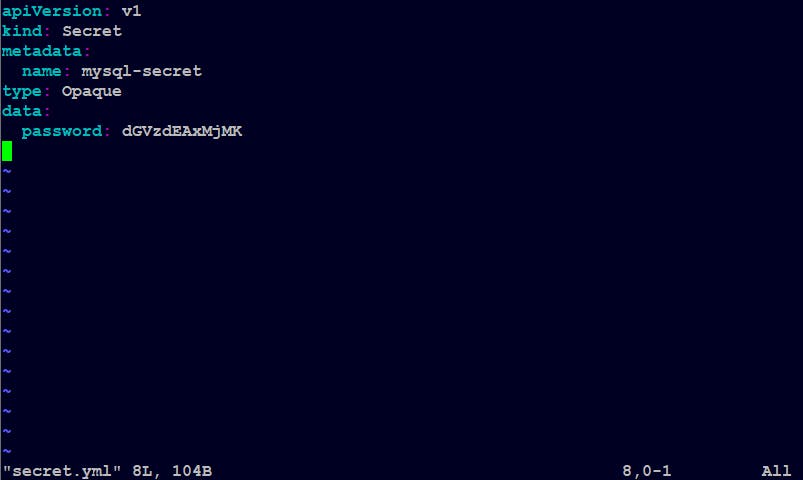
For your info, if you ever want to decode and see the actual password enter the below command:
echo "dGVzdEAxMjMK" | base64 --decode
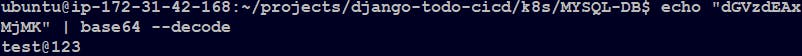
Now, Let's apply the secret.yml file
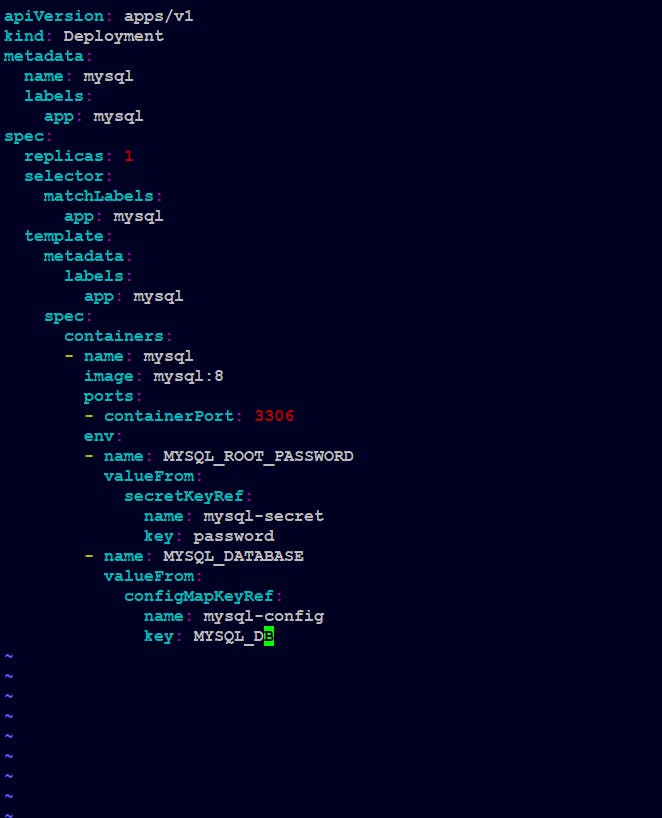
Deployment file with secret and configmap
As, our "secret.yml" and "configmap.yml" files are ready we can now make a "deployment.yml" file which will use values from secret.yml and configmap.yml

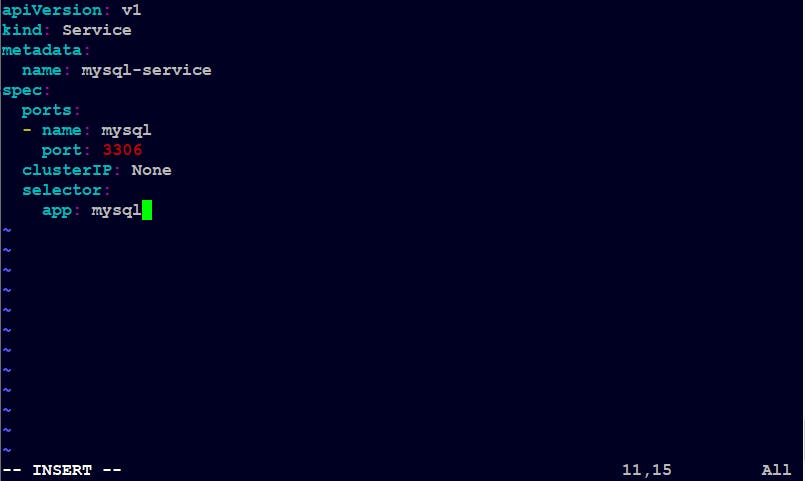
Now, to expose port 3306 we need to create a service.yml file

Thank you for reading!
Happy Learning!